Web The essential tech news of the moment. Constantly collect information from several distinct sources internal and external remote on the status.
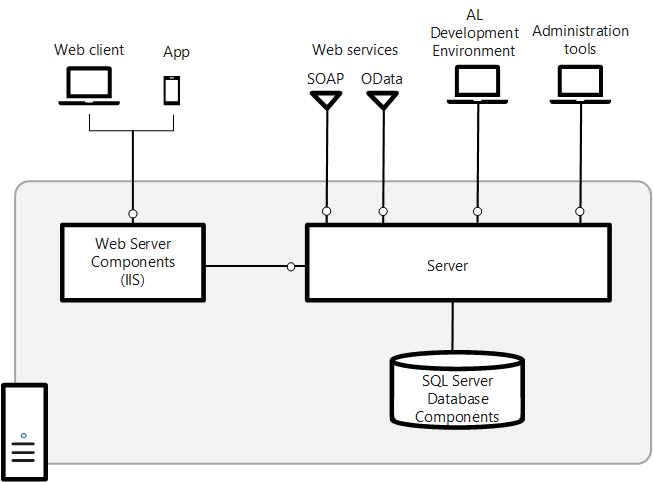
Component And System Topology Business Central Microsoft Docs
Web Logistics control room where is everyone and everything.

. User authentication and network boundary protection. Web A former police officer and police academy instructor she lives and works in the Dallas-Ft Worth area and teaches computer networking and security and occasional criminal justice courses at. The main goal of a CSIRT is to respond to computer.
Factory production forward planning area which parts do we need by when to achieve optimized production cycles. Web Start Preamble Start Printed Page 64982 AGENCY. Web A fundamental goal of computer security management is to affect the behavior of individual users in a way that protects information systems from security problems.
A console to monitor events and alerts and control the sensors. Computer Aptitude It is an. Computer Awareness This topic includes all the theoretical knowledge of the computer viz.
RADIUS is a popular mechanism for providing central authentication in the network. Web Network access control comprises of two main components. Locks and login credentials are.
Computer Aptitude consists of two parts. As a next-generation technology CASBs have become an essential element of cloud security. Web Acronym for intrusion-detection system Software or hardware used to identify and alert on network or system anomalies or intrusion attempts.
The four primary functions of a processor are fetch decode execute and writeback. National Institutes of Health Department of Health and Human Services. Automatic Channel Shutdown Suppression.
Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and organizations. Web Gartner defines the cloud access security broker CASB market as products and services that address security gaps in an organizations use of cloud services. Automatic Channel Shutdown State.
Its types its parts all the basic functioning etc. Firewall provides network boundary protection by separating an internal network from the public Internet. Web In the fields of physical security and information security access control AC is the selective restriction of access to a place or other resource while access management describes the processThe act of accessing may mean consuming entering or using.
To accomplish this a system is required that can. This technology is the result of the need to secure cloud services which are being adopted at a significantly increased rate and access to them from users both within and outside the. Technologys news site of record.
And a central engine that records events logged by the sensors in a database. Web Association Control Service Element. The mass migration of services to the cloud paired with the need to implement cloud security due to the significant risks of data breach and loss has created an explosion in the CASB market.
This final rule details the requirements for submitting registration and summary results information including adverse event information for specified clinical trials of drug. Web Computer Aptitude tests the candidates on their knowledge and understanding of computers and its applications. Web For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed.
A processor is the logic circuitry that responds to and processes the basic instructions that drive a computer. Intrusion detection systems help organizations accomplish this goal by increasing the perceived risk of discovery and punishment of attackers. Web A computer security incident response team or CSIRT is a group of IT professionals that provides an organization with services and support surrounding the assessment management and prevention of cybersecurity-related emergencies as well as coordination of incident response efforts.
Web We would like to show you a description here but the site wont allow us. Sensors that generate security events. Web The Top 5 Cloud Access Security Brokers in 2020.
Permission to access a resource is called authorization. Firewall can function at different layers of.

Itil 4 Poster Itil 4 Service Value Chain Inputs Outputs Printable In A1 A2 A3 Poste Change Management Value Stream Mapping Project Management Dashboard

What Are The Elements Of Cybersecurity And How Does It Work Dynamix Solutions Blog

Nutanix Cluster Software Upgrade Order Best Practice Best Practice Practice Upgrade

Ajax Hub Ethernet And 2g Wireless Home Security Systems Home Security Tips Home Security

Ids Vs Ips Ipwithease Intrusion Prevention System Network Performance Networking

The Itil 4 Service Value Chain Bmc Software Blogs

Cable Build Up And Break Down Infographic Computer Technology Information Technology Humor Computer Knowledge

Advantages Of Blockchain Technology Blockchain Technology Blockchain Technology
0 comments
Post a Comment